Ping Of Death Windows Cmd . The options parameter is crucial, as its value establishes the size. Web ping of death. Web to do this, the attacker will use the ping command on the command line and create the package. Web here’s what a ping of death looks like on windows and linux : The ping command is usually used to test the availability of a network resource. It works by sending small. Does the ping of death still work? Web the attacker will use the ping command on the command line to create a ping of death packet. It was successful as this created a lot of cmd consoles which were continuously pinging. Here is how a ping of death looks on windows and.
from www.ionos.com
The ping command is usually used to test the availability of a network resource. The options parameter is crucial, as its value establishes the size. Web here’s what a ping of death looks like on windows and linux : It was successful as this created a lot of cmd consoles which were continuously pinging. Does the ping of death still work? Web to do this, the attacker will use the ping command on the command line and create the package. Here is how a ping of death looks on windows and. Web the attacker will use the ping command on the command line to create a ping of death packet. Web ping of death. It works by sending small.
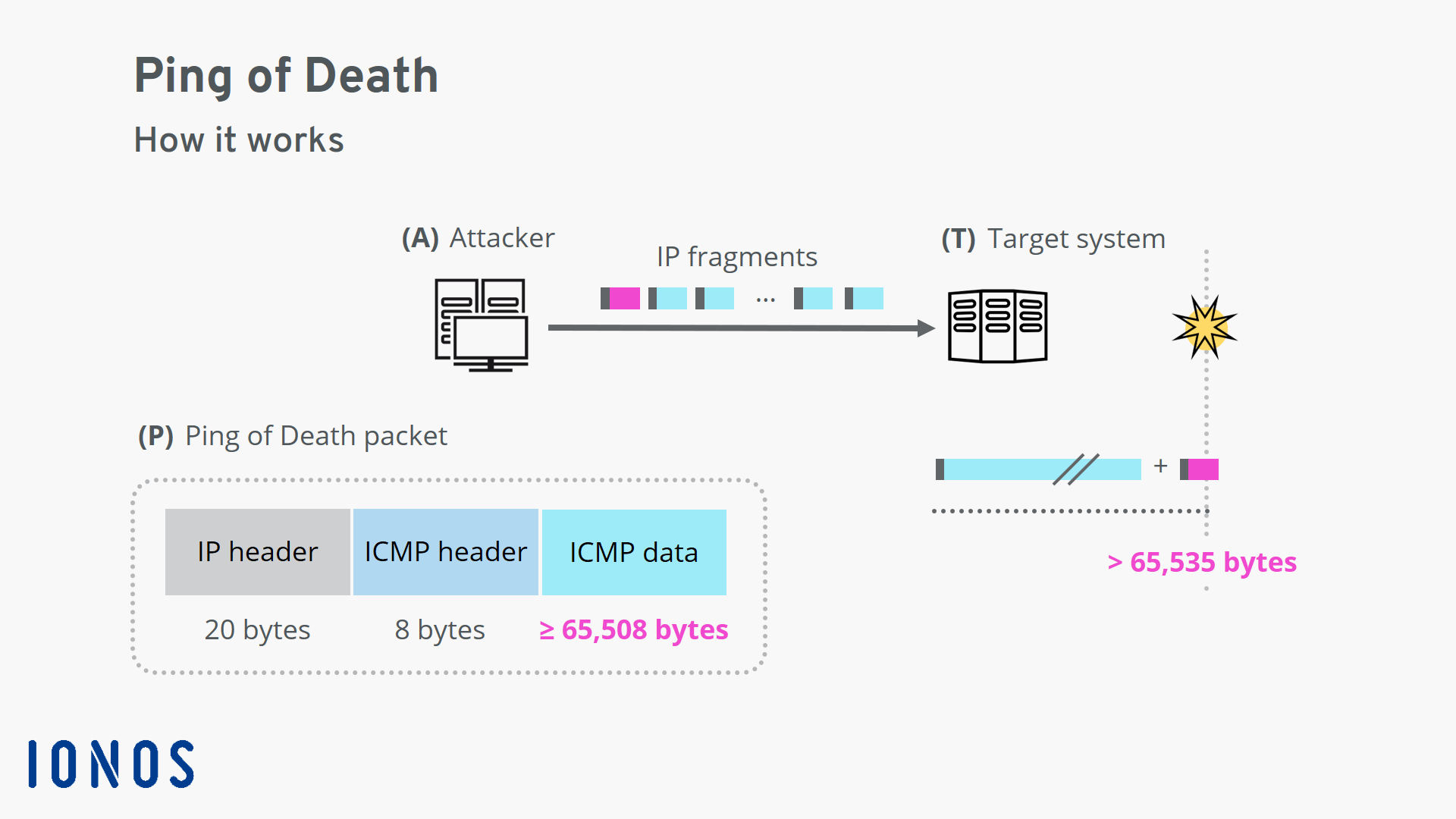
Ping of death an attack strategy from the early days of the
Ping Of Death Windows Cmd The ping command is usually used to test the availability of a network resource. Web the attacker will use the ping command on the command line to create a ping of death packet. Does the ping of death still work? The ping command is usually used to test the availability of a network resource. Here is how a ping of death looks on windows and. It works by sending small. The options parameter is crucial, as its value establishes the size. It was successful as this created a lot of cmd consoles which were continuously pinging. Web to do this, the attacker will use the ping command on the command line and create the package. Web here’s what a ping of death looks like on windows and linux : Web ping of death.
From www.insecure.in
Ping of Death Attack Definition, Detection, and Prevention Ping Of Death Windows Cmd It works by sending small. Web to do this, the attacker will use the ping command on the command line and create the package. Web here’s what a ping of death looks like on windows and linux : The options parameter is crucial, as its value establishes the size. Web ping of death. It was successful as this created a. Ping Of Death Windows Cmd.
From www.vrogue.co
√ Apa Itu Ping? Ini Penjelasan Serta Fungsi Ping (lengkap) Inilah Arti Ping Of Death Windows Cmd The ping command is usually used to test the availability of a network resource. It works by sending small. Does the ping of death still work? Web here’s what a ping of death looks like on windows and linux : It was successful as this created a lot of cmd consoles which were continuously pinging. Web to do this, the. Ping Of Death Windows Cmd.
From infosec-train.blogspot.com
What is the Ping of Death Attack? Ping Of Death Windows Cmd Does the ping of death still work? The ping command is usually used to test the availability of a network resource. Here is how a ping of death looks on windows and. Web to do this, the attacker will use the ping command on the command line and create the package. Web ping of death. It works by sending small.. Ping Of Death Windows Cmd.
From gospeedcheck.com
How to check your ping with CMD? 2 Quick steps (with Pictures) Ping Of Death Windows Cmd Web the attacker will use the ping command on the command line to create a ping of death packet. The ping command is usually used to test the availability of a network resource. Here is how a ping of death looks on windows and. Web ping of death. Web to do this, the attacker will use the ping command on. Ping Of Death Windows Cmd.
From www.youtube.com
Lecture 34Ping Of Death Attack YouTube Ping Of Death Windows Cmd Web here’s what a ping of death looks like on windows and linux : Here is how a ping of death looks on windows and. Web ping of death. Does the ping of death still work? The ping command is usually used to test the availability of a network resource. It works by sending small. Web the attacker will use. Ping Of Death Windows Cmd.
From fastestvpn.com
Ping of Death Attack Apa Artinya & Cara Mencegahnya Ping Of Death Windows Cmd Here is how a ping of death looks on windows and. The options parameter is crucial, as its value establishes the size. Does the ping of death still work? Web ping of death. The ping command is usually used to test the availability of a network resource. Web to do this, the attacker will use the ping command on the. Ping Of Death Windows Cmd.
From ceedpbki.blob.core.windows.net
What Does The Command Ping Localhost Do at Perkins blog Ping Of Death Windows Cmd Does the ping of death still work? Web the attacker will use the ping command on the command line to create a ping of death packet. Here is how a ping of death looks on windows and. Web to do this, the attacker will use the ping command on the command line and create the package. Web here’s what a. Ping Of Death Windows Cmd.
From www.youtube.com
what is ping of death attack in Network security YouTube Ping Of Death Windows Cmd The ping command is usually used to test the availability of a network resource. Web to do this, the attacker will use the ping command on the command line and create the package. It was successful as this created a lot of cmd consoles which were continuously pinging. Web here’s what a ping of death looks like on windows and. Ping Of Death Windows Cmd.
From www.ionos.com
Ping of death an attack strategy from the early days of the Ping Of Death Windows Cmd The options parameter is crucial, as its value establishes the size. Web here’s what a ping of death looks like on windows and linux : It works by sending small. Does the ping of death still work? Here is how a ping of death looks on windows and. It was successful as this created a lot of cmd consoles which. Ping Of Death Windows Cmd.
From www.youtube.com
como hacer el ping de la muerte en cmd YouTube Ping Of Death Windows Cmd Web ping of death. It was successful as this created a lot of cmd consoles which were continuously pinging. Web to do this, the attacker will use the ping command on the command line and create the package. Here is how a ping of death looks on windows and. Does the ping of death still work? The options parameter is. Ping Of Death Windows Cmd.
From www.configserverfirewall.com
CMD Ping Command Test Network Connectivity and Latency Ping Of Death Windows Cmd Does the ping of death still work? It was successful as this created a lot of cmd consoles which were continuously pinging. The ping command is usually used to test the availability of a network resource. Web to do this, the attacker will use the ping command on the command line and create the package. Web the attacker will use. Ping Of Death Windows Cmd.
From community.tp-link.com
Large Ping & Ping of Death Attacks Business Community Ping Of Death Windows Cmd Web to do this, the attacker will use the ping command on the command line and create the package. It was successful as this created a lot of cmd consoles which were continuously pinging. Here is how a ping of death looks on windows and. Web here’s what a ping of death looks like on windows and linux : Does. Ping Of Death Windows Cmd.
From www.youtube.com
How to Use Ping Command in CMD on Windows 10/8/7/XP Pinging Ping Of Death Windows Cmd Web here’s what a ping of death looks like on windows and linux : It works by sending small. Does the ping of death still work? Web ping of death. The ping command is usually used to test the availability of a network resource. Here is how a ping of death looks on windows and. It was successful as this. Ping Of Death Windows Cmd.
From www.cloudns.net
Ping of Death (PoD) What is it, and how does it work? ClouDNS Blog Ping Of Death Windows Cmd The ping command is usually used to test the availability of a network resource. Web here’s what a ping of death looks like on windows and linux : Does the ping of death still work? Here is how a ping of death looks on windows and. The options parameter is crucial, as its value establishes the size. It was successful. Ping Of Death Windows Cmd.
From www.slideserve.com
PPT Lecture 05 IP Security PowerPoint Presentation, free download Ping Of Death Windows Cmd Web to do this, the attacker will use the ping command on the command line and create the package. Here is how a ping of death looks on windows and. It was successful as this created a lot of cmd consoles which were continuously pinging. The ping command is usually used to test the availability of a network resource. Web. Ping Of Death Windows Cmd.
From github.com
GitHub Killeroo/PowerPing Advanced commandline ping tool Ping Of Death Windows Cmd Here is how a ping of death looks on windows and. It works by sending small. The options parameter is crucial, as its value establishes the size. Web the attacker will use the ping command on the command line to create a ping of death packet. Web ping of death. Web to do this, the attacker will use the ping. Ping Of Death Windows Cmd.
From japaneseclass.jp
ping of death Ping of death JapaneseClass.jp Ping Of Death Windows Cmd Does the ping of death still work? The options parameter is crucial, as its value establishes the size. Web ping of death. Web the attacker will use the ping command on the command line to create a ping of death packet. Web to do this, the attacker will use the ping command on the command line and create the package.. Ping Of Death Windows Cmd.
From dxoiokmtf.blob.core.windows.net
How To Disable Ping Command In Windows 10 at Stephen Clarke blog Ping Of Death Windows Cmd Web the attacker will use the ping command on the command line to create a ping of death packet. Web here’s what a ping of death looks like on windows and linux : It was successful as this created a lot of cmd consoles which were continuously pinging. Web to do this, the attacker will use the ping command on. Ping Of Death Windows Cmd.